Checklist
Please ensure that you have turned in everything.
I asked that everyone turn in a title/abstract (which everyone did),
plus a representative picture, slide, or screen capture,
and that you make your code available to me electronically.
| name | code available? | picture? |
| Satish Puri | yes | |
| Xiaxia Yu | yes | yes |
| David Bolding | yes | yes |
| Gang Shen | yes | yes |
| Semra Kul | yes | yes |
| Sunny Shakya | yes | yes |
| Mingyuan Yan | yes | yes |
| Sanish Rai | yes | yes |
| Mark Daniel Gibbons | yes | yes |
| Chad Griffith | yes | yes |
| Tariku Ahmed | yes | |
| Sanghoon Lee | yes | yes |
| Guoliang Liu | yes | yes |
| Zainab Haydari | yes | yes |
CSc 8270 Presentations, Fall 2011
Satish Puri,
Convolution implementation on GPU for Magnetic Resonance Imaging
I have implemented a digital signal processing algorithm in Graphics
Processing Unit (GPU). To my best knowledge, MATLAB does not directly take
advantage of parallel processing capabilities of a graphics processing
unit. As such, it is interesting to explore GPU implementation of existing
MATLAB function e.g. *conv* and *conv2* (convolution).
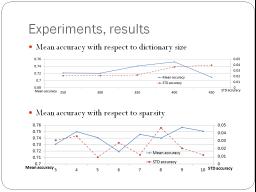
Xiaxia Yu,
Sparse Dictionary for HIV-1 Protease Drug Resistance Prediction
The sparse signal representation is an emerging research area in the
recent years. Indeed, it has been realized that the sparsity is a hidden
prior information for most of the signals in the physical world and the
related phylosophy and algorithms have been applied in a wide range of
areas such as signal acqusition, signal representation, pattern
classification, etc., and have achieved very exciting results.
Therefore, in this project, we aim at applying such technique in our
project of the HIV-1 protease drug resistance prediction. Specifically,
we learn the dictionaries to represent the drug resistant and non-drug
resistant mutants of the HIV-1 protease. Then, given a new protease, the
learned dictionaries are used to sparsely represent the new protease.
The protease is then classified according to the error of the sparse
representations. The proposed method is tested on 360 mutants of HIV-1
protease to demonstrate the algorithm's accuracy and robustness.
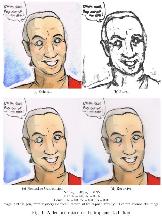
David Bolding,
Applying the novel image-blurring technique
from my paper summary
My presentations is about applying the novel image-blurring technique
from my paper summary. In mathematical terms, it's a coordinate
transform across a manifold. It's much simpler in implementation
terms. I'll probably have some snide comments about unnecessarily
dressing up a published result with mathematical language.
I got the blur to work; they also included other filters, like a
colorizer and an edge-detecter. I'll probably try to add those over the
break, so I have something more to present.
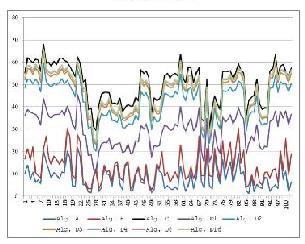
Gang Shen,
A Study of Huffman Lossless Image Compression Algorithms
The project experimented various Huffman lossless image compression
algorithms. A new Huffman lossless image compression program is also
proposed and tested. Experiments show the proposed new algorithm
achieved better performance than all tested compression algorithms
including a published "Folding" based compression
algorithm.
Semra Kul,
Segmentation of Intervertebral Discs in Spine MRI
In the project, a method for segmentation of intervertebral discs from the
surrounding body parts in spine MRI (Magnetic Resonance Imaging) is
presented. The morphological image processing (thresholding, erosion,
dilation) are applied to sagittal (vertical) spine MRI samples. The aim
of the project is to provide a preliminary work for further segmantation
of the spine in diagnosis of disc related diseases.

Sunny Shakya,
Segmenting an Image using Snakes
Description - Snake is the widely used method for segmenting an image or
detecting an object boundary. I have implemented Snake in MATLAB and Since
snake has very limited capture range, an extra pressure force is added to
increase its range of capture and the resulting snake is known as Balloon
Snake. I have also compared my implementation with Gradient Vector Flow
Snake. Experiments shows that Snake can accurately segment an image
provided snake is initialized close to the region of interest.

Mingyuan Yan,
Image Denoising Using Diffusion and BayesShrink-based Wavelet
Transform
Among all the wavelet based image denoising technique, wavelet image
denoising based threshold filtering is the most popular due to its
low computation, easily implementing and so on. In this paper, the
author first introduces some important preliminary about image
denoising. After that, An algorithm based on wavelet and diffusion
is implemented followed its performance evaluation by comparing with
four other approaches. The experiment result shows that the diffusion
and wavelet-based method outperforms the traditional thresholding
method and local mean based method is some cases. However, the
visual result shows that the image quality after denoising is
far from satisfying compared with the clean image quality.

Sanish Rai,
Image stitching
Image stitching finds it use in creating a single map or
photo by combining multiple small fragments. The method discussed
works by matching multiple images sequentially and finding invariant
local features. These features are used to find match between the
images. The use of invariant local features makes the method
insensitive to the ordering, orientation, scale and illumination of
the multiple images.
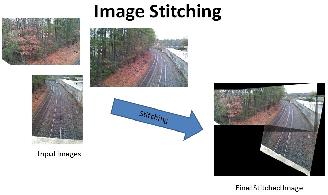
Mark Daniel Gibbons,
JWRMark - A Java Library for Watermarking
Watermarking has been gaining traction in recent
years to be able to detect who distributed an image
[9] and to ensure content is legitimate [8]. A Java library,
JWRMark, is proposed to provide an easy means for Java
developers to embed a watermark within an image. Two
algorithms are included with the first release. The first
algorithm is one which simply adds the watermark to the
LL band of an image decomposed by a Discrete Wavelet
Transform (DWT). The second algorithm embeds the image
within the singular values of an image decomposed by
the DWT and Discrete Cosine Transform (DCT). An emphasis
is put on being able to easily add new algorithms
with reusable code.
[8] Lintao Lv, Liang Hao, and Hui Lv, =93Resisting RST Watermarking
Algorithm for Image Content Authentication,=94 2010
Second International Conference on Networks Security,
Wireless Communications and Trusted Computing, Volume 2,
Pages 361-364, April 2010.
[9] K A Navas, Ajay Matthews Cheriyan, M Lekshmi, S Archana
Tampy, and M Sasikumar, =93DWT-DCT-SVD Based Watermarking,=94
3rd International Conference on Communication
Systems Software and Middleware and Workshops, Pages 271-
274, January 2008.
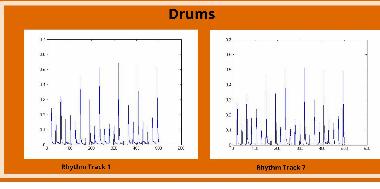
Chad Griffith,
Isolating and Analyzing Rhythm Tracks For Use in Beat Detection Systems
Beat detection systems' core component is being able to generate
reliable and acceptable rhythm tracks for use in beat analysis.
However, there has not been a lot of research in the specific area of
generating rhythm tracks, only the overall beat tracking system. This
paper gives a short introduction on beat tracking methods, rhythm
track generation, a short proposal for a middle man system, and short
analysis of various rhythm tracks. Emphasis is directed towards more
research in generating various quality rhythm tracks as well as manual
and automatic analysis of these generated tracks.
Tariku Ahmed,
A Research on Frequencies out of Human Hearing Range
Like Dog Whistle and Ultrasonic Pest
Record sound frequency made by dog whistle and Ultrasonic Pest Repellent,
so that they become human audio-able. Based on this perhaps examine if it is
possible to develop apps that could be used to irritate robbers not only
that, but also if we could develop an app that would equipped our home
security system, mobile phone, and car key chains to deter any intruders.
Sanghoon Lee,
Utilizing Morphological Processing for Moment Invariants
This paper focuses on the image preprocessing, especially morphological
image processing for a variety of hand sign images. In order to provide
the various hand signs, Kodaly hand signs are used in preprocessing step.
The fathomable point in hand is seldom considered in the preprocessing.
A gray-scale morphological technique is utilized in the preprocessing
step to reduce the computational burden of feature extraction. This
work has slightly lower error rates for extracting the feature vector
than the processing on raw binary images.
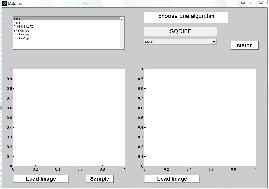
Guoliang Liu,
Image matching using area-based matching method(tested through
MATLAB GUI)
Image matching method includes area-based matching methods or say
template matching methods and feature-based methods. In this project, I
realize five area-based matching methods relative to correlation-based
and square deviation based methods. Through Matlab GUI, it is possible
to test the accuracy and efficiency of each method actively and apparently.
In the future work, matching in the video can be done but not in matlab
since the image matching I implemented is not efficient. Double loops or
more overlapped loops can be deadly in Matlab. In another aspect, Matlab
GUI still have bugs and need to be be corrected and improved.
Zainab Haydari,
Signal analysis for differentiating healthy and pathological voices
In this paper I have used a method of voice signal analysis for
differentiating healthy and unhealthy voices based on predictability
measures. The met hod measures the predictive power (PP) that uses
the relative entropy between signal and its prediction error to obtain
the information about the predictability of the patient=92s voice
production system, and is based on the wavelet decomposition. I
have implemented this method and I have applied it to three groups
of signals, i.e., healthy, nodule, and vocal cysts. The results show
that the predictive power of pathologic groups are less than that of
healthy group . This decrease is a result of increase of intricacy
and irregularity of pathologic signals.
-Michael Weeks









